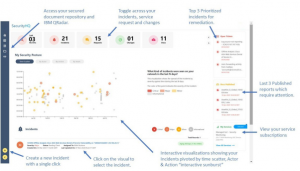
An Incident Management Platform should, ideally, be an arena for security orchestration and response tooling, to have live information at the users fingertips, to rapidly identify and limit the impact of security threats and risks. This needs to include 24/7 threat monitoring, detection, and targeted response, powered by real-time log analytics, with security orchestration, automation and response tooling for investigation, threat hunting and response. A successful Incident Management Platform should combine threat intelligence and human expertise for advanced analytics and to accurately contextualize events.
Key Objectives of an Incident Management Platform
The four critical objectives of an Incident Management Platform are to simplify incident handling by enabling collaboration, prioritization, integration, and visibility, often with third-party tools.
- Collaboration
An Incident Management Platform is a platform for collaboration with the Security Operation Centre team, to share incident data and coordinate a response plan.
Interoperability is key. A unified interface is used to provide seamless access and collaboration via remote SOC’s, and between tooling (SIEM, EDR, SOAR), IT security teams for the handling of playbooks for incident handling, vulnerability management and change management.
Members can collaborate across IT and Security teams, to prioritize, remediate and rapidly respond to security risks. Escalate and action tasks to ITSM tooling, such as ServiceNow, Jira, and Remedy.
- Prioritization
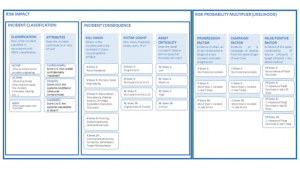
Incidents should be categorized against MITRE ATT & CK and assigned their risk level, based on the combination of CIA attributes, asset criticality and the normal behavior of the asset.
Algorithms calculate incident risk by considering the classification attributes, in accordance with VERIS, that contribute to the magnitude of the problem, such as the Kill Chain, MITRE ATT&CK, victim counts, asset criticality, and more. Analysts then apply predictive risk factors that increase or decrease the degree of risk. The output is a contextualized risk assessment for each incident. So that it is clear what needs to be tackled first.
- Integration
Bidirectional integration, with tools such as QRadar, Resilient and ServiceNow, can be used to present and track incidents. Incident response requires advanced analysis, combined with an accurate assessment, categorization, and a playbook for investigation and response.
- Visibility
Challenges and patterns based on incident metrics should be illustrated to Illuminate data with interactive visuals, via data-driven documents, so that information can be presented quickly and intuitively. By inspecting data visually through a time series graph or sunburst chart, for instance, the analyst can drill down into the data to identify an accident, its trends, and how this information relates to other artifacts.
How Does this Impact Operational Effectiveness?
- By using an Incident Management platform, organizations optimize their time to respond to security incidents.
- Collaboration is enhanced by allowing stakeholders (technical and non-technical) to collaborate on incidents.
- SOC teams are able to deliver multi-tenant managed security services using a single collaboration tool, which can be white-labeled.
For more information on SecurityHQ’s award winning platform, read The Value of a Managed Incident Response Platform, or speak to one of our specialists here.
In response to winning the 2021 IBM Grocer Award for Outstanding Security Solution, Feras Tappuni, CEO of SecurityHQ reported that “Security Operations demand collaboration across staff, department and third parties, armed with rich data and playbooks. SecurityHQ provides a unified security management platform to orchestrate incident response, prioritise actions, connect resources and visualise risk”.
About SecurityHQ
SecurityHQ prides itself on its global reputation as an advanced Managed Security Service Provider, delivering superior engineering-led solutions to clients around the world. By combining dedicated security experts, cutting-edge technology and processes, clients receive an enterprise grade experience that ensures that all IT virtual assets, cloud, and traditional infrastructures, are protected.
Authors: Eleanor Barlow, Content Manager, SecurityHQ
Facebook: https://www.facebook.com/Sechq
Twitter: https://twitter.com/security_hq
LinkedIn: https://www.linkedin.com/company/securityhq/